
Process of Rooting
Rooting is the process which allows the users of smartphones, tablets and other devices running the Android operating system to gain privileged access also known as root access over various Android subsystems.

Rooting is the process which allows the users of smartphones, tablets and other devices running the Android operating system to gain privileged access also known as root access over various Android subsystems.
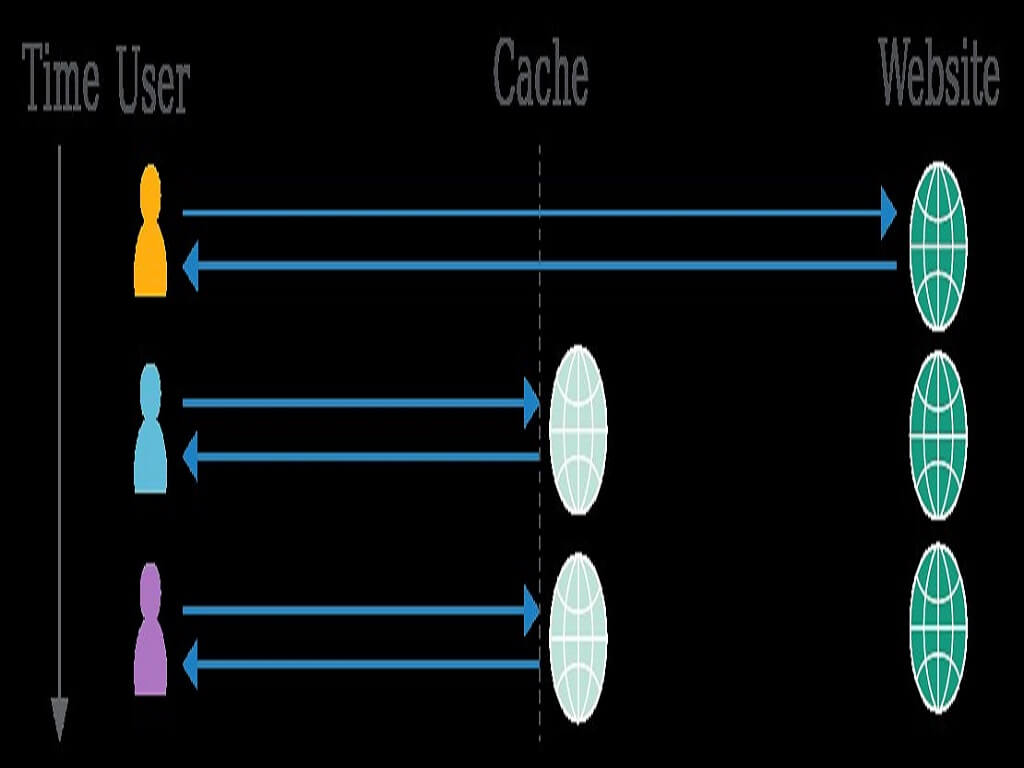
Web cache poisoning has long been an elusive vulnerability, a 'theoretical' threat used mostly to scare developers into obediently patching issues that nobody could actually exploit.
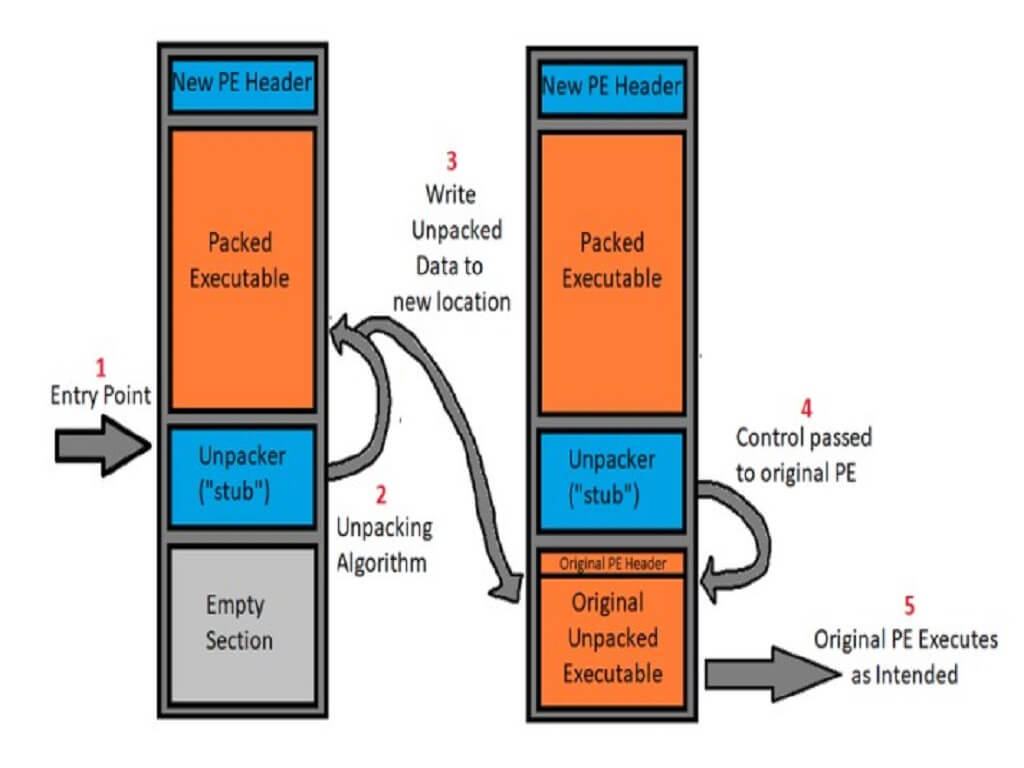
Distributing an executable in a compressed or obfuscated state, making it more difficult to detect statically analyse and reverse engineer.
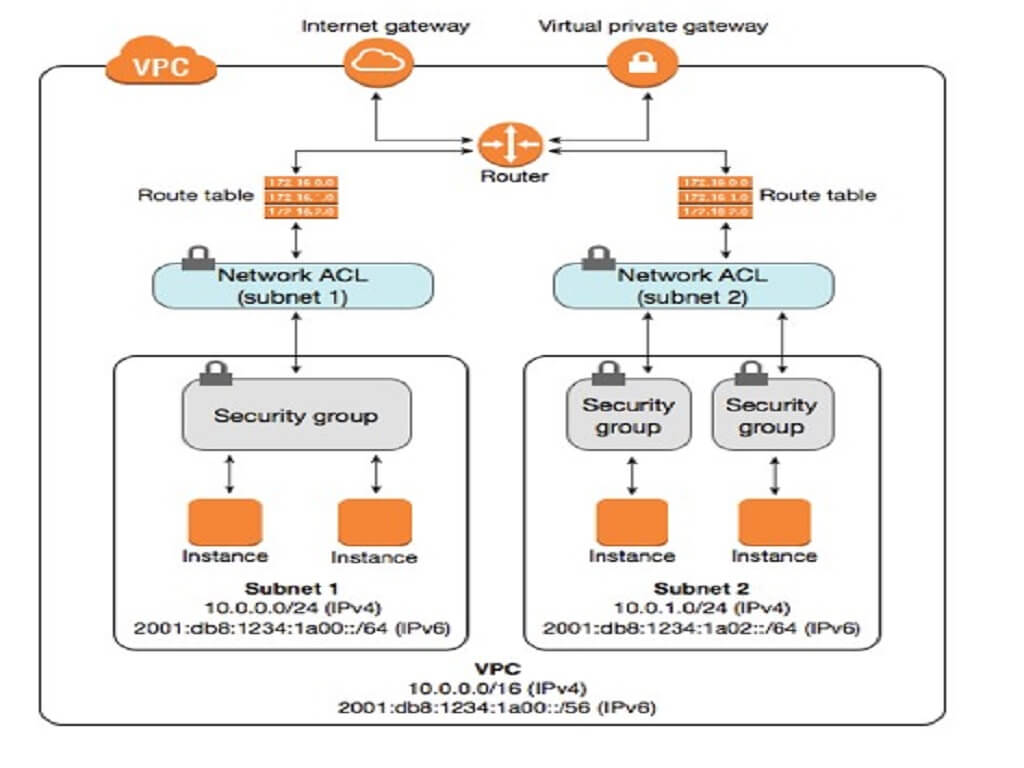
When we create a VPC, AWS automatically creates a default security group and default NACL for us.
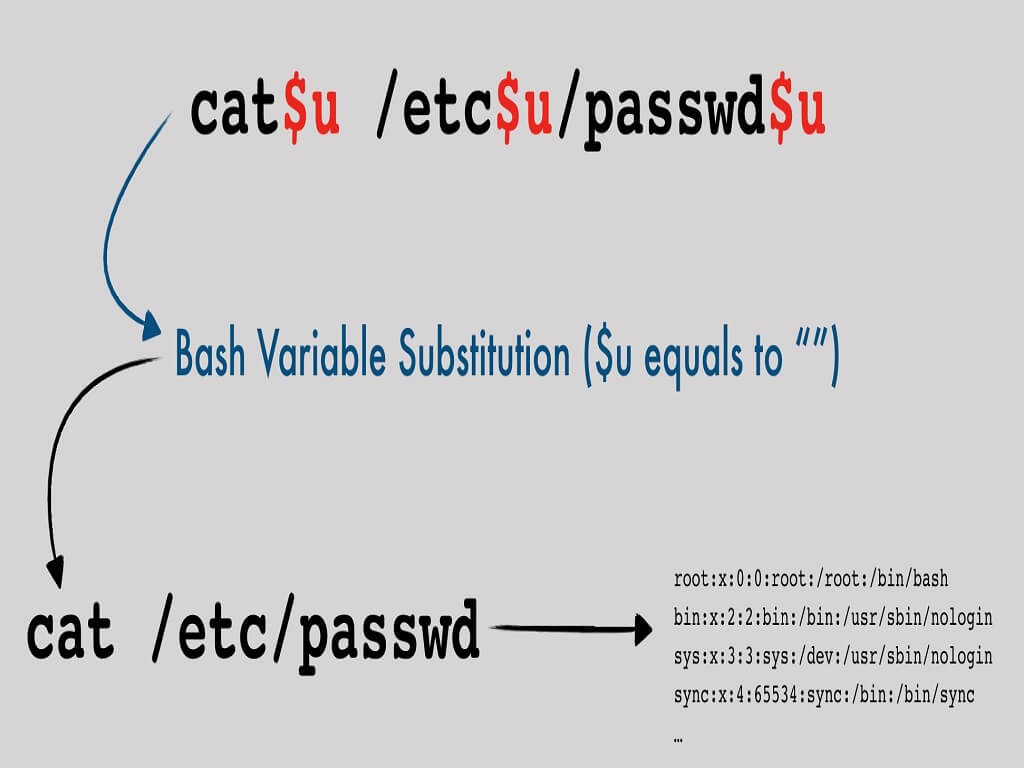
In the last two articles of this series of "Web Application Firewall (WAF) evasion techniques", we have looked at how to bypass a WAF rule set exploiting a Remote Command Execution on a Linux system by abusing of the bash globing process.

A USB drop attack occurs when an attacker strategically places a USB device somewhere, potentially containing malicious code, with the intention of someone taking it and plugging it into a computer.
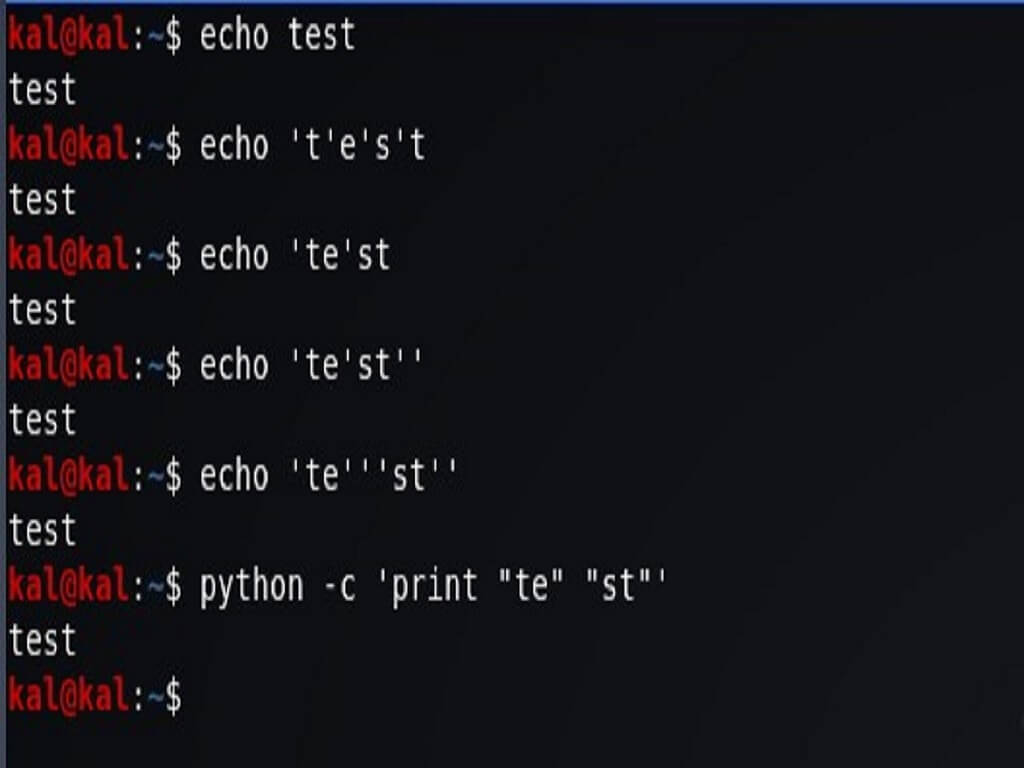
This is a great technique, and it works well when the target WAF has a low paranoia level that allows asterisk * and hyphen characters.
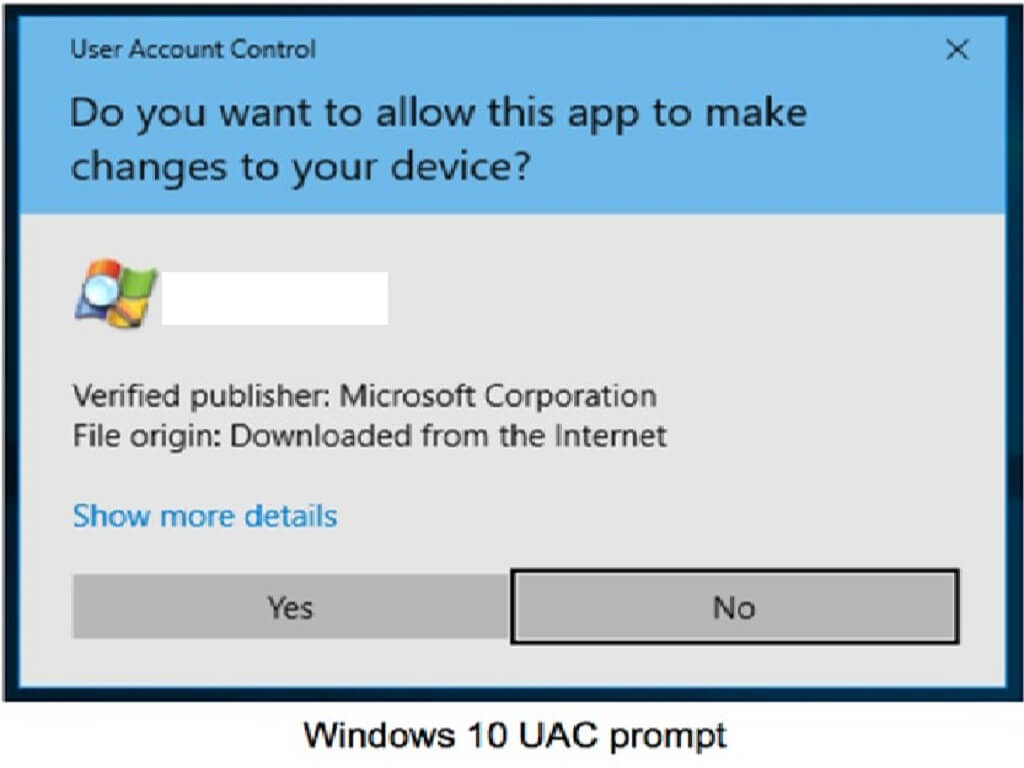
User Account Control (UAC) is a Windows feature that helps to prevent unauthorized changes to the system. This blog will show how a threat actor can silently execute privileged actions that modify the system while bypassing this security control.