By using an automatic testing toolkit, a crew of South Korean teachers has found 30 vulnerabilities within the file add mechanisms used by 23 open-source net functions, boards, retailer builders, and content material administration methods (CMS).
When present in real-world web apps, these types of vulnerabilities allow hackers to exploit file upload forms and plant malicious files on a victim's servers. These files could be used to execute code on a website, weaken existing security settings, or function as backdoors, allowing hackers full control over a server.
All of the file-uploading vulnerabilities had been found utilizing FUSE, a brand new automated penetration testing instrument created to uncover UFU (unrestricted file add) and UEFU (unrestricted executable file add) vulnerabilities in PHP functions.
The research team said that prior to building FUSE they analysed past file upload bugs and identified the eight most common exploitation patterns and techniques. FUSE consists of these eight patterns, along with five new variations devised by the research team (see M5, M7, M9, M10, and M13 in the table below).
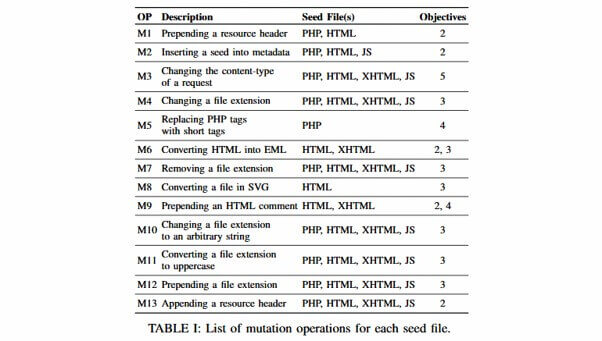
After they constructed FUSE, the analysis crew mentioned they chose the 33 hottest net apps, together with the likes of boards, CMSs, enterprise merchandise, and on-line retailer builders.
The research team, which consisted of academics from the Korea Advanced Institute of Science and Technology Constitution (KAIST) and the Electronics and Telecommunications Research Institute (ETRI), said they individually tested FUSE against the latest versions of those web apps (at the time of the tests, in February 2019).
Utilizing a sequence of automated requests, the researchers exploited file add mechanisms within the 33 net apps in a try to plant varied kinds of malicious information (PHP, JS, HTML, XHTML, htaccess) inside one of many examined net apps. KAIST and ETRI researchers mentioned the exams unearthed 30 file add bugs impacting 23 of the 33 functions they examined.
The tests took place in February 2019, and the table may contain web apps that have received updates during the past year. However, KAIST and ETRI researchers said that not all projects have patched the bugs they found, and some of the projects highlighted in yellow above may still contain one or more file upload bugs.
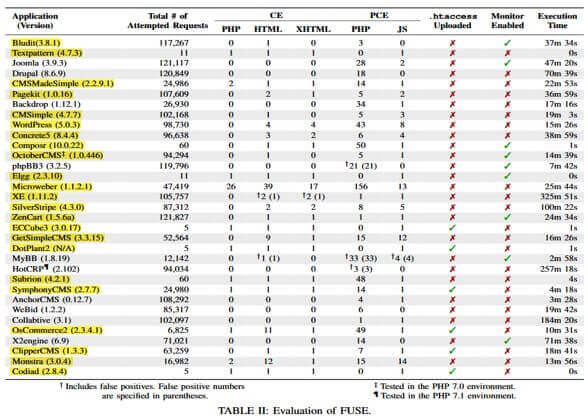
“We reported all of the 30 UEFU vulnerabilities to the corresponding distributors and obtained 15 CVEs from 9 functions,” the analysis crew mentioned.
“Eight vulnerabilities from 5 distributors have been patched. 5 vulnerabilities from 4 distributors, together with WordPress, confirmed that they’d handle the reported vulnerabilities,” researchers added.
"15 bugs are awaiting confirmation from the corresponding vendors. Two vendors declined to patch the reported bugs."
Because the researchers clarify, a purpose why some distributors did not prioritize patches — or downright refused to patch — was as a result of 14 of the 30 bugs required admin entry to take advantage of, a standard that many tasks do not think about to be a danger since a hacker with admin entry can hijack a server by professional CMS options anyway.
But while KAIST and ETRI researchers listed the web apps that contained bugs, they didn't list which projects patched and which did not -- in an attempt to prevent attacks against web apps that did not ship a patch yet.





