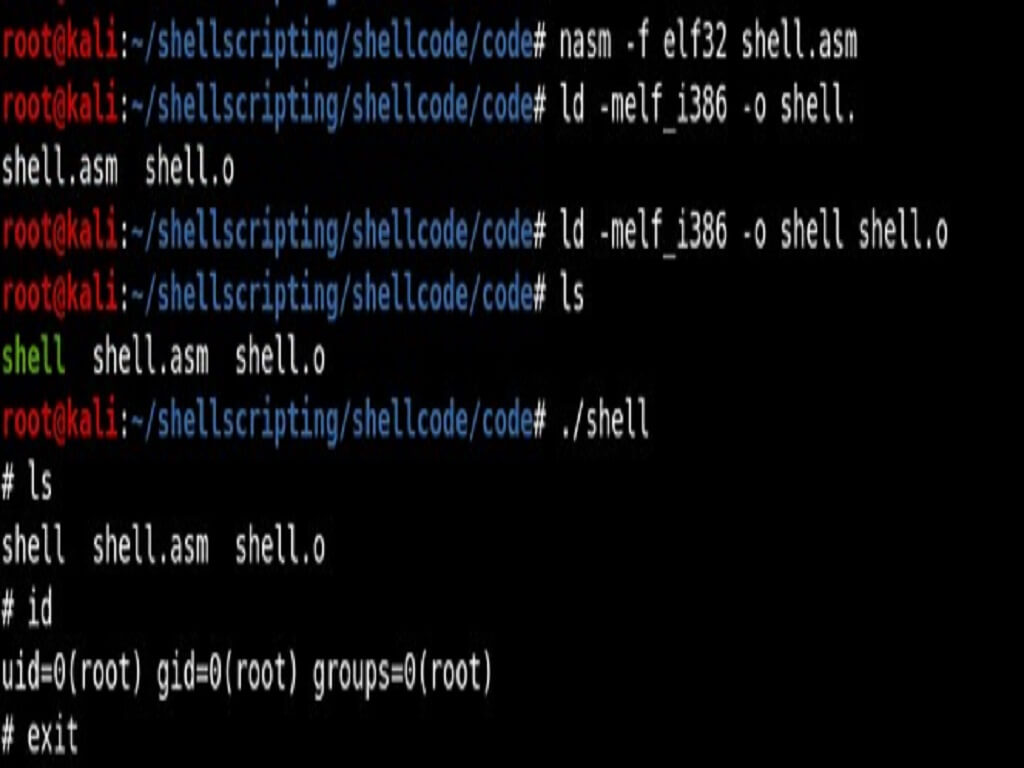
PetitPotam is an NTLM relay attack that could be used against a Windows server, forcing it to share credentials and then relaying these to generate an authentication certificate. This method could be used by an attacker to take complete control of a domain from a domain controller. A fresh NTLM relay attack, known as PetitPotam, was discovered by French security researcher Gilles Lionel. On July 18, Giles posted a proof-of-concept (PoC) to his GitHub account. According to Giles, the flaw makes Windows hosts use the MS-EFSRPC EfsRpcOpenFileRaw function to authenticate to other computers.
Introduction
A new Technology LAN Manager (NTLM) relay attack method known as PetitPotam has been discovered by security researchers. It could force a server, including domain controllers (DC), to authenticate against a remote NTLM server under an attacker's control. PetitPotam forces a target server to start the NTLM authentication process by using a valid feature of the Microsoft Encrypting File System Remote Protocol (MS-EFSRPC) API. The target's NTLM credentials are used to create a signed certificate by relaying the NTLM credentials to Active Directory Certificate Services (ADCS).
Impacts
Successful exploitation gives an attacker an authentication certificate that can be used to access domain services as a DC and the potential to compromise the entire domain.
Signs of Petitpotam Vulnerability
In situations where the servers hosting Active Directory Certificate Servers have not been configured with the appropriate defences, you as an organisation may be vulnerable to the threat or attack. Using the EFSRPC remote authentication protocol, PetitPotam is a vulnerability that allows attackers to launch an NTLM relay attack and take over your Windows domain.
An attacker pushes the use of NTLM and sends an EFSPRC connection request to a Domain Controller (rather than Kerberos or safer authentication alternatives). After completing this NTLM authentication, the attacker launches an NTLM relay in order to steal the password.
The attackers' primary focus is on the IIS servers that are installed over Domain Controllers and used for certificate service web enrolment. He can easily break web enrolment, steal the certificate, and gain domain authority once he has the domain credentials.
If you don’t want to be a victim of this vulnerability, restricting or limiting the NTLM incoming traffic is a better choice rather than disabling NTLM in the whole network.
You can mitigate this by
The simplest way to mitigate, according to Microsoft, is to disable NTLM authentication on the Windows domain controller, which administrators can do to prevent this attack. Admins can do this by following the instructions in the Network security documentation: NTLM authentication in this domain is restricted.
The simplest way to mitigate, according to Microsoft, is to disable NTLM authentication on the Windows domain controller, which administrators can do to prevent this attack. Admins can do this by following the instructions in the Network security documentation: NTLM authentication in this domain is restricted.
Administrators are instructed to disable NTLM on any AD CS Servers in the domain using the group policy if it cannot be disabled for compatibility reasons. Network safety NTLM traffic coming in should be restricted.
Microsoft advises setting "Network security: Restrict NTLM: Incoming NTLM traffic" to "Deny All Accounts" or "Deny All domain accounts" in order to configure this GPO. To do this, open Group Policy and navigate to Computer Configuration -> Windows Settings -> Security Settings -> Local Policies -> Security Options. Using the setting "Network security: Restrict NTLM: Add server exceptions in this domain," you can add exceptions as required.
On AD CS servers in the domain running Certificate Authority Web Enrolment or Certificate Enrolment Web Service, administrators can also disable NTLM for Internet Information Services.
Conclusion
Certified-Pre Owned is a valuable white paper focusing on various ADCS vulnerabilities and through the means of our blog, we aim to create awareness about these attacks so that organisations can understand, implement and patch such unknown and unobserved weaknesses. Hope you liked the article. Thanks for reading.