As a Pen tester, we need to know as much as possible about the Internal Network Architecture. The (sub) Network cartography allows the attacker to discover the largest number of potential machines to compromise.
DCOM (Distributed Component Object Model) is a set of Microsoft concepts and program interfaces in which client program objects can request services from server program objects on other computers in a network. DCOM is based on the Component Object Model (COM), which provides a set of interfaces allowing clients and servers to communicate within the same computer (i.e., running Windows 95 or a later version).
Exploiting RPC Method
Examining the traffic flow between the server and the client in a DCOM based product and dissecting the exchanged frames, we will probably see both an IOXIDResolver interface and the RPC methods such as SimplePing() and ServerAlive2().
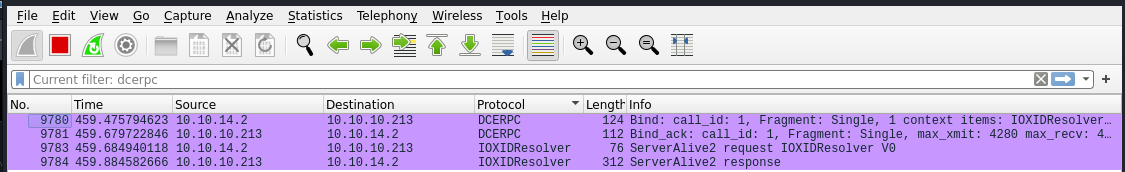
IOXIDResolver RPC
The OXID Resolver is a service that runs on every machine that supports COM+. It performs two important duties:
- It stores the RPC string bindings that are necessary to connect with remote objects and provides them to local clients.
- It sends ping messages to remote objects for which the local machine has clients and receives ping messages for objects running on the local machine. This aspect of the OXID Resolver supports the COM+ garbage collection mechanism.
DCE-RPC request allows you to bind with the IOXIDResolver interface. It’s IID is “99fcfec4–5260–101b-bbcb-00aa0021347a” then we will focus on the ServerAlive2() method. The latter is part of IOXIDResolver interface.
According to the MS-DCOM documentation, the ServerAlive2() method is described and the parameters having the meanings as follows

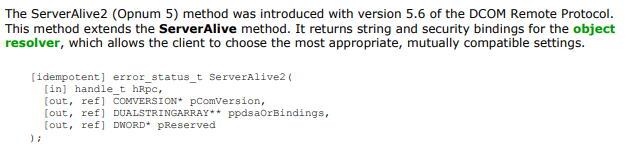
ServerAlive2 Method described in section 3.1.2.5.1.6 IObjectExporter::ServerAlive2
- hRpc:An RPC binding handle
- pComVersion:Contains COMVERSION of the Object resolver
- ppdsaOrBindings:Contains string and security bindings of the object resolver
- pReserved:Contains zero and must be ignore by recipient
In this Context, the ppdsaOrBindings is the output parameter of interest. It’s type is an array of DUALSTRINGARRAY which is defined as follows

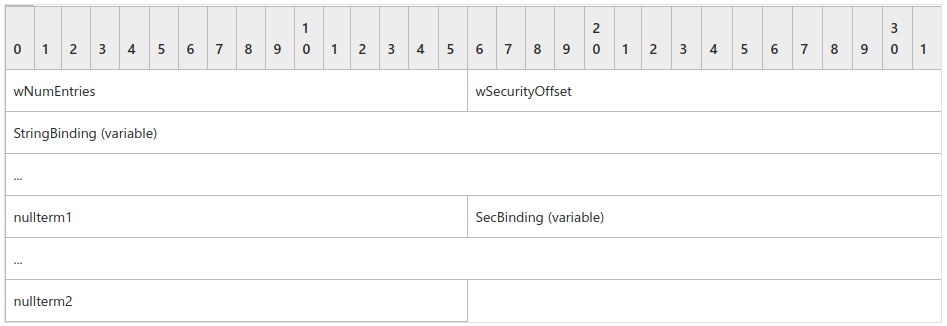
MS-DCOM DUALSTRINGARRAY structure
The protocol uses this structure as a fundamental means of specifying RPC addressability and security information for either an object resolver or an object exporter.
Below picture shows the DUALSTRINGARRAY response returned from the ServerAlive2().

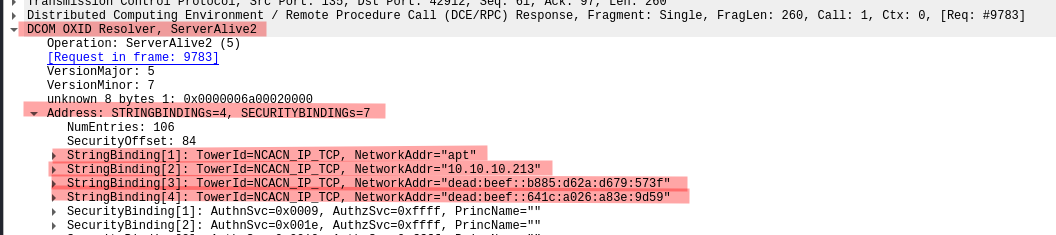
ServerAlive2() RPC Response
The remote OXID resolver returned six DUALSTRINGARRAY entries composed of:
- The network machine name
- Five IP addresses
From this response, we will be able to collect remote network interfaces.
Retrieving network or string bindings of the object resolver, not to be confused with the endpoint bindings can be used to reach an object exporter and can be retrieved from a conventional call to the ResolveOxid() method.
Obtaining an OXID requires to be authenticated. However, the ServerAlive2() method, held by the IOXIDResolver interface, also provides a part of these bindings. That is the remote IP adresses without a TCP port number. This time, owning an OXID is no longer necessary, no authentication is required.
Python Tool
We can develop a tool to collect these bindings to identify the remote network interfaces using python 3
from impacket.dcerpc.v5 import transport
from impacket.dcerpc.v5.rpcrt import RPC_C_AUTHN_LEVEL_NONE as authLevel
from impacket.dcerpc.v5.dcomrt import IObjectExporterip = "192.168.1.7"stringBinding = r'ncacn_ip_tcp:%s' % ip
rpctransport = transport.DCERPCTransportFactory(stringBinding)objExporter = IObjectExporter(portmap)
bindings = objExporter.ServerAlive2()print("[*] Retrieving network interface of " + ip)
for address in bindings:
NetworkAddr = address['aNetworkAddr']
print("Address: " + NetworkAddr)
The above code does not require any user credentials. This is a powerful and useful trick when a pentester attempts to get a network cartography.
Result of the tool when targeting a Windows 10 Pro as shown

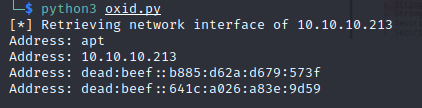
IOXID network interface tool output