Cyber 2.0'
Blocking the spread of cyber-attacks
Core Technology
Based on Mathematical Chaos Model that cannot be breached. Know more about Chaos mathematics
The Problem
The main damage is the spread of cyber-attacks across the organization
Core Philosophy
The Mathematical Chaos Engine creates a form of chaos balance among the authorized computers. It Scrambles the Out going Traffic from the Authorized Computers and descrambles it on the computer it enters. On the other hand it doesn’t scramble outgoing traffic from the unauthorized computers and again de-scrambles it on the computer it enters. Therefore any unauthorized computer will not be able to communicate within the network, simply because it will not be conceived as such by the protected computers
We Don’t Miss Any New Attack
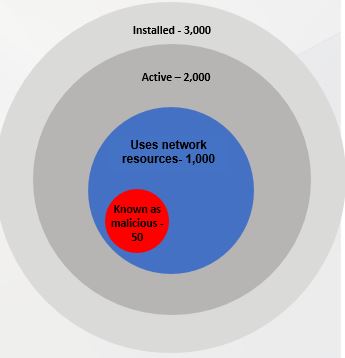
- Cyber 2.0 automatically maps all software: those that were installed (3,000), that are active (2,000), that move across the network (1,000)
- Removing all software that are known as malicious (50)
- Cyber 2.0 approved the rest (950)
- Cyber 2.0 blocks every software that was not approved
- IT manager gets the whole service from Cyber 2.0
Core Design
Designed in such a way that even if it is attacked or removed from the infected system, it can still protect the spread/lateral movement of the attack from the infected computer into the organization as the Cyber 2.0 agent

Every Ordinary
Attack Against
Cyber 2.0
Will fail
- Bypassing Cyber 2.0
- Deactivating Cyber 2.0
- Adding malicious software to the list
- Malicious software using other software
- Man in the middle
Our Technology Combines Several Capabilities






